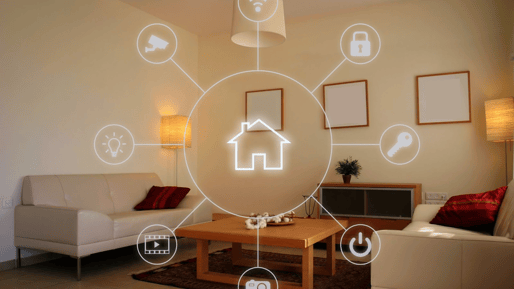
Data transfer
Data transferred across smart home systems must still be encrypted to prevent personal data from being accessed by hackers who gain unauthorized access to home networks.

Device security
It’s important for devices to not only be secure in their present state, but to remain secure even as they undergo numerous iterations of software updates to stay relevant.

Documentation and data use
Device documentation must fulfill legal requirements such as user data protection and child data protection to be legally distributed within target markets.

Online communication
Passwords to personal accounts and devices must be protected through IP protocol encryption to prevent household devices from being controlled by cyberattackers.

Wireless connection
The lifeblood that connects smart home systems, wireless networks need to cover sufficient ground and be flexible enough to navigate complex layouts. In addition, there must also be sufficient safeguards in place to prevent personal networks from being breached.

Vulnerability assessments
GRL provides comprehensive vulnerability assessments that cover all these aspects and more to ensure that your smart home IoT systems not only remain airtight against evolving threats but are also fully compliant with Market Access requirements such as ETSI EN 303 645, ITSARs under ComSec India, and other domestic and international requirements.


.png?width=711&height=400&name=TC%20(6).png)


.png?width=500&height=281&name=TC%20(8).png)