Granite River Labs (GRL)
By Ray Yang – Test Engineer, GRL (Taipei)
HDCP (High-Bandwidth Digital Content Protection), is a technical specification for digital content protection formulated by Intel in 2003. It is mainly used to prevent the illegal recording of high-definition movie content transmitted through digital interfaces, such as DVI, HDMI® and DisplayPort™. Using this technology, audio and video content is encrypted to prevent illegal recorders from restoring and stealing the original HD audio and video.
If HDCP is not available on any end of the Transmitter, Receiver or Repeater link, it is not possible to play high-definition audio and video content. The picture quality will be reduced to 480p or, even worse, the playback will fail completely. With the increasing demand for high-definition content, technology that supports digital encryption is becoming more and more popular. Currently, most of the consumer multimedia audio-visual and entertainment products on the market, such as transmitters, receivers and video game consoles, use HDCP.
Manufacturers that want to use this protection technology must first join the Digital Content Protection (DCP) Association and pay an annual fee of USD 15,000. They then purchase a “KEY” for content encryption, with the cost depending on the quantity purchased (see Table 1).
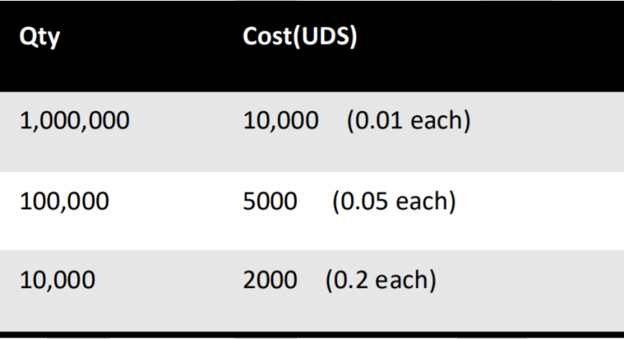
Table 1: Cost of HDCP Keys
The "KEY" contains a special Key Selection Vector (KSV), which is a critical link in the HDCP encryption process. The KSV is a binary value consisting of twenty "0s" and twenty "1s". The Transmitter and the Receiver check each other's KSV to ensure that the connection is legitimate. Each device has a unique set of KEYs, which is saved in a list of DCP Association.
To prevent the KEY from being cracked or leaked, a "revocation list" which contains all cracked or leaked KSVs has been set up. The Transmitter will check whether the Receiver's KSV is on the list. If so, the connection is considered to be illegal and playback of the video and audio content is immediately interrupted.
An HDCP system features three key devices – the Transmitter, the Receiver and the Repeater. According to the HDCP1.x specification, up to seven layers of repeaters and 128 devices can be connected in the system (see Figure 1. below).
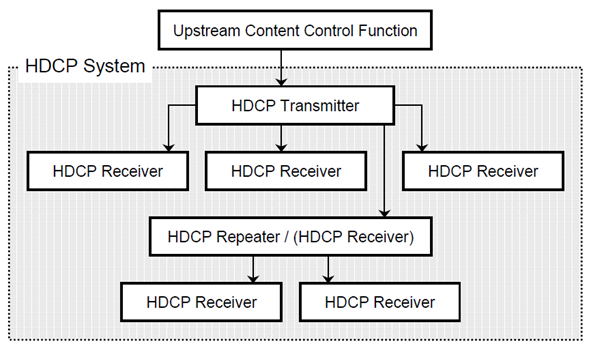
Figure 1: HDCP System Connections (source: HDCP Specification Rev1_4)
Based on the Authentication Protocol, the Transmitter and Receiver exchange keys. This allows the Transmitter to confirm whether the Receiver is an authorized device which is allowed to receive HDCP-encrypted digital video and audio content. As part of this authentication protocol, both devices use Device Private Keys authorized by the DCP Organization to execute encryption calculations. The result is a “Km" – a shared secret value which is used to confirm whether the devices are Authorized.
There are three key steps in the authentication process:
1. First part of Authentication Protocol
2. Second part of Authentication Protocol
3. Third part of Authentication Protocol
Authentication Protocol – Part 1
In Part 1, the Keys are exchanged between a Transmitter and a Receiver/Repeater to ensure that the connection between these devices is legitimate.
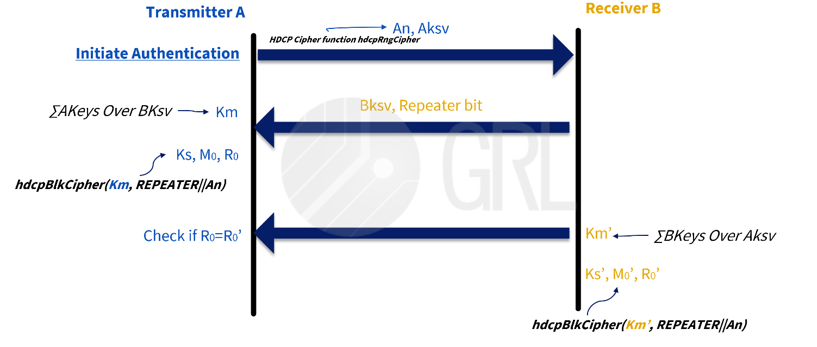
Figure 2: HDCP Authentication Protocol – Part 1
Steps:
- The Transmitter can initiate HDCP authentication at any time.
- The Transmitter sends an AKsv and an An to the Receiver. (AKsv = the KSV of the Transmitter. An = a random 64-bit value).
- The Receiver responds by sending a Bksv and a REPEATER bit (Bksv = the KSV of the Receiver. The REPEATER bit indicates whether the receiver is a repeater).
- The Km (shared secret value) is calculated by a 56-bit binary addition, with the secret device key corresponding to the returned KSV of the device connected to the Transmitter as the parameter. The Km of the connected device is calculated using the same method.
For the HDCP cipher unit, Ks, M0, and R0 are calculated using parameters such as Km, repeater ||An.
Ks: Session key – a 56-bit secret key in the HDCP cipher unit.
M0: A 64-bit secret value, which is used in Part 2 of the authentication protocol.
R0: A 16-bit return value, which is sent back by the Receiver to the Transmitter, indicating that the authentication exchange was successful.
- If R0 = R0', HDCP decryption will begin when the authentication is completed.
- The Transmitter must not read the R0' value earlier than 100ms after writing Aksv.
Authentication Protocol – Part 2
In Part 2, when the subordinate device is a Repeater, all KSVs of the downstream devices are collected and reported to the upstream devices. This step will only be performed when the downstream device is a Repeater.
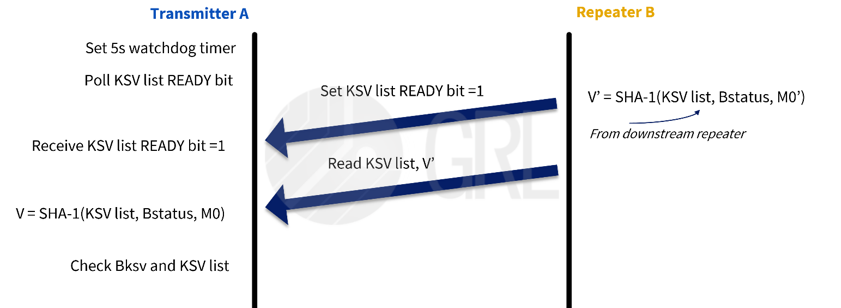
Figure 3: HDCP Authentication Protocol – Part 2
Steps:
- The Transmitter sets a 5-second waiting time to ensure that the steps are completed within 5 seconds, and requests the status of the lower-level KSV list and Ready bit.
- The Repeater at the lower level sends Ready bit=1 and the collected KSV list to the Transmitter.
- The Repeater at the lower level uses the collected KSV list, Bstatus and M0' calculated in Part 1 of the authentication protocol, and the SHA-1 calculation method to calculate V'.
- The Repeater at the upper level calculates V in the same way, and compares it with the V' returned by the Repeater at the lower level. If V≠V', it is impossible to send Ready bit=1 to the Transmitter within the 5 seconds, indicating that there is a problem with the integrity of the KSV list.
- If V=V', the Transmitter checks the KSV list, V and V' again. In the following cases, it terminates the connection and retries Part 1 of the authentication process:
-
- The size of KSV list exceeds the Transmitter's capacity.
- V≠V’
- The Transmitter has not received Ready bit =1 within five seconds.
In addition to collecting the complete list of KSVs, the Repeater will also report the DEVICE_COUNT and DEPTH in Bstatus to the Transmitter, so that the Transmitter can check whether the number of layers in the whole HDCP system and the number of the connected devices exceed the upper limit.
Authentication Protocol – Part 3
In Part 3, the system will confirm whether the encryption frequency and sequence of the two HDCP devices are consistent and synchronous. At the same time it generates an additional authentication mechanism.
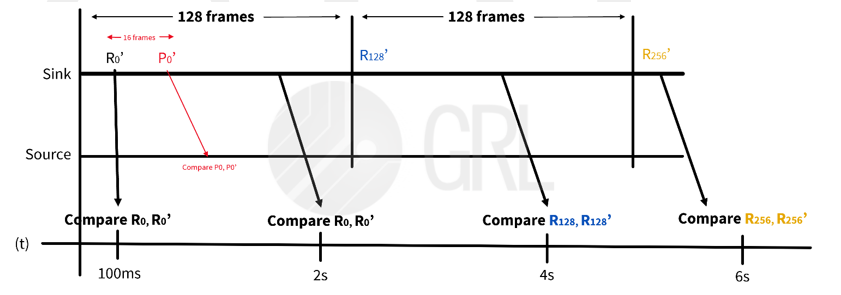 Figure 4: HDCP Authentication Protocol – Part 3
Figure 4: HDCP Authentication Protocol – Part 3
Steps:
- Calculate Ki, Mi and Ri on both devices
Ki: A 56-bit value, which initializes decryption and encryption of the HDCP cipher unit
Mi: A 64-bit value, which initializes the HDCP cipher unit
Ri: A 16-bit value which confirms whether the Transmitter and the Receiver are legitimate
- The “i” is the frame number. It will be calculated when Part 1 of the authentication protocol is completed and the first encrypted frame starts. Each frame, or each encrypted frame, is incremented upwards.
- Ri and Ri’ will be recalculated every 128 frames.
- The Transmitter compares Ri with Ri’ every two seconds.
- The Transmitter needs to read Ri’ within 1ms.
- If the device supports HDCP 1 features, the Pj value will be checked once every 16 frames. If three consecutive Pj errors are encountered during the check, a pixel transmission error will be identified.
Conclusion
If consumers want to watch digital multimedia audio and video content, such as a Blu-ray Disc that is protected by HDCP, both the DVD player and the receiver (TV and Monitor) must have built-in keys and the ability to execute the above authentication steps. Otherwise the high-resolution digital video content may not be available.
As part of additions to HDCP1.4 conducted in response to the update of HDMI2.0 (the most recent version is HDMI2.1), the DPC association published a protection mechanism for HDCP2.2 in 2013. This was further updated to HDCP2.3 in 2018.
References
- High-bandwidth Digital Content Protection System, Revision 1.4. 8 July, 2009
- High-bandwidth Digital Content Protection Specification Compliance Test Specification, Revision 1.2. November 18, 2009
Author
Ray Yang – Test Engineer, GRL (Taipei)
A graduate of National Taiwan University of Science and Technology’s Department of Chemical Engineering, Ray Yang is a Test Engineer at GRL (Taipei). He has accumulated more than three years of experience in HDMI testing and is familiar with HDMI, MIPI, V by One and other testing specifications. He helps customers clarify HDMI problems and successfully obtain certification.


